You may have a number of smart Internet-connected devices in your home, but do you have any ideas what these IoT devices are doing? Who are they talking to? What are they sending?
For instance, let’s say you have a Roku TV and that you are live-streaming the Bloomberg Channel without interacting with the TV otherwise. Do you know that the Bloomberg Channel could be communicating with 13 different advertising and tracking servers in the background? Or let’s say you have a smart Geeni light bulb. Are you aware that it could be communicating with a Chinese company every 30 seconds even while you are not using the bulb?
To learn more about your own IoT devices, you could set up a wireless hotspot and run Wireshark, but is there an easier approach to monitor the network traffic of IoT devices?
We can help! Today, we release IoT Inspector, a open-source tool that lets you inspect IoT traffic in your home network right from the browser. With a one-click install process, you can watch how your IoT devices watch you within minutes of setup.
Download now: https://inspector.engineering.nyu.edu/site/post/getting-started/
What we found using IoT Inspector
We used IoT Inspector to monitor a number of IoT devices in our lab. Here are a few examples of security and privacy problems that we have found.
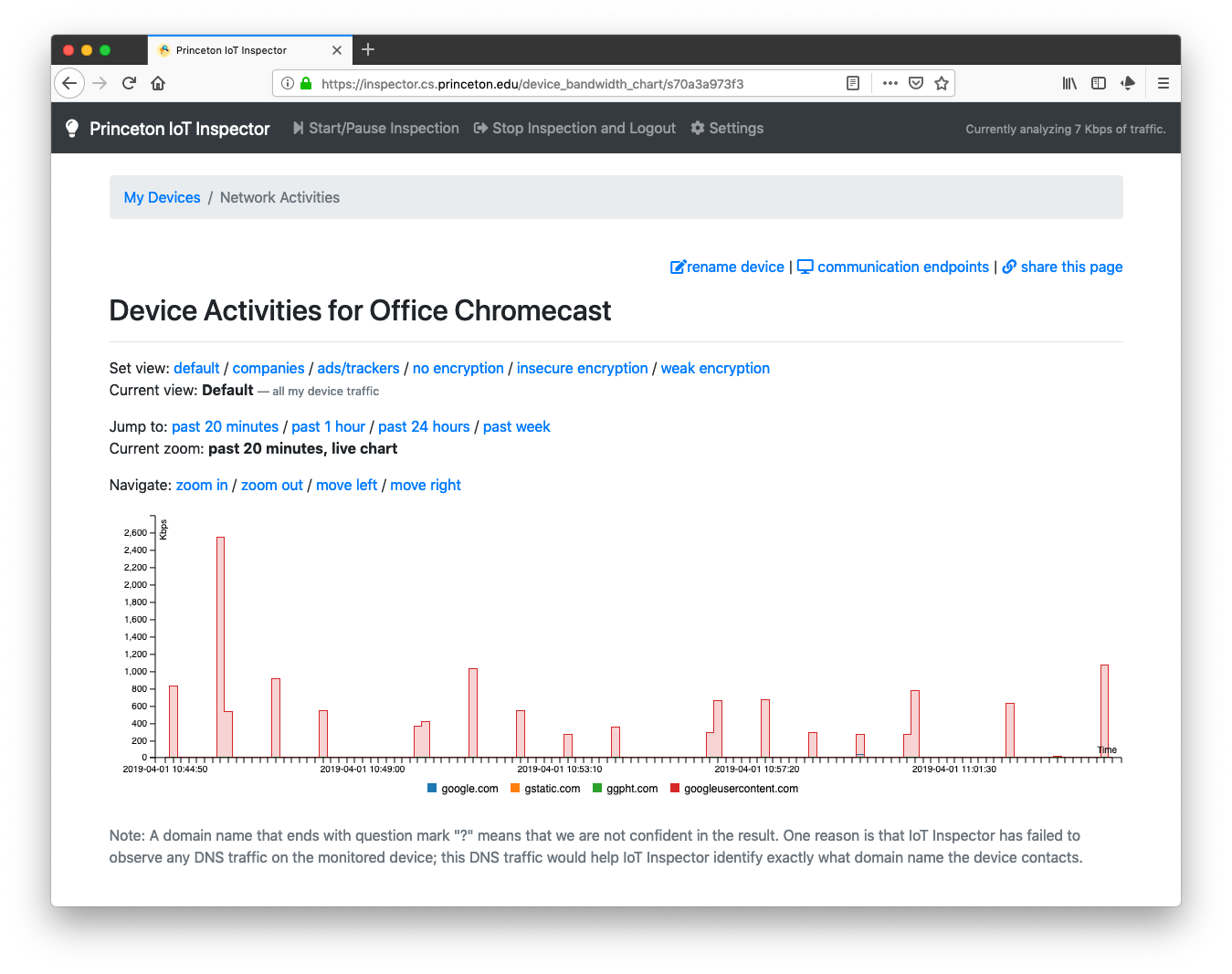
Chromecast
Even when we were not actively using Chromecast, the device constantly contacted Google’s servers. Click here to see a video of how IoT Inspector monitors the Chromecast in real time.
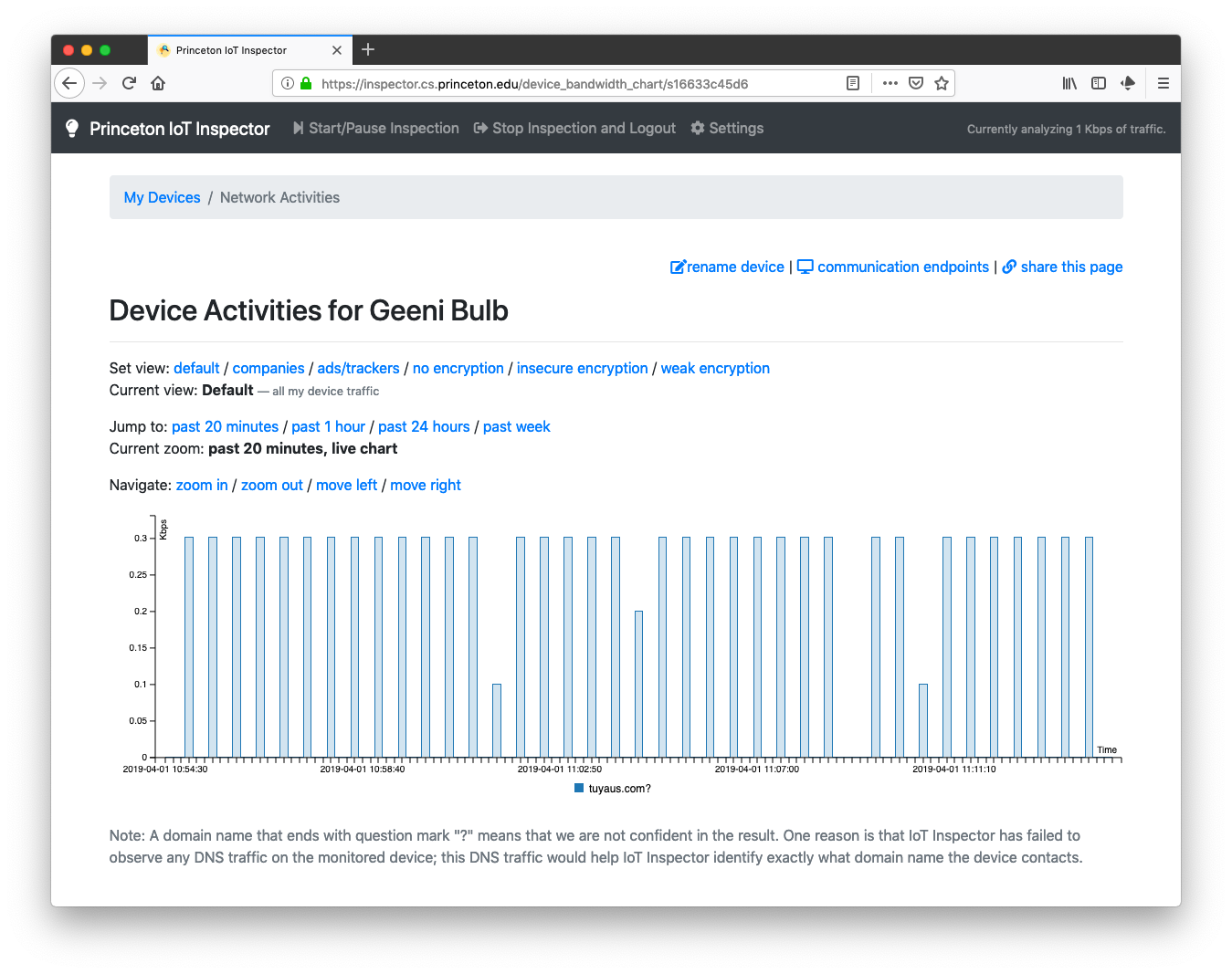
Smart Bulb
We also monitored a Geeni smart bulb with IoT Inspector. Like Chromecast, this device was constantly communicating with the cloud — sending/receiving traffic with tuyaus.com every few seconds. Of particular note, tuyaus.com is operated by TuYa Inc., a China-based company that offers a platform that controls IoT devices.
More findings in later blog posts
In the next few blog posts, we will show how we used IoT Inspector to…
learn how smart TVs contacted advertising/tracking services as we watched TVs;
discover how a “secure” communication from a smart TV to the cloud may not be secure at all;
and find that a WiFi-enabled camera was communicating with a number of countries, including Russia, Czechia, India, and Brazil
Why did we build IoT Inspector?
We have developed IoT Inspector to help consumers of IoT devices as well as academic researchers.
For consumers
Many IoT devices are proprietary and close-source. This lack of transparency makes it difficult for consumers to decide whether to trust their devices’ security and privacy practices (or the lack thereof).
To learn more about their devices, a user could do one or more of the following:
Read Consumer Reports or similar IoT review sites such as YourThings or Shitdex. Downside: The range of devices reviewed may be limited.
Run antivirus software that comes with network scanners (e.g., Avast WiFi Inspector). Downside: Difficult to show if a device is actually hacked or sending data to third parties, because such scanners do not observe actual network traffic on IoT devices (i.e., off-path).
Buy high-end home routers such as Bitdefender Box, which can typically analyze actual network traffic (i.e., on-path) and warn users (e.g., via smart phone apps) of any security/privacy issues. Downside: These routers are typically expensive.
Set up a wireless hotspot to analyze IoT traffic with WireShark. Downside: This technique requires technical expertise.
To mitigate the problems above, we have developed IoT Inspector with the following design goals:
able to analyze actual network traffic of a wide range of IoT devices
requiring no special hardware or complicated setup (i.e., users can run IoT Inspector directly on their computers)
requiring minimal technical expertise while helping users identify any security/privacy issues on their IoT devices
free and open source desktop client
For researchers
We have also built IoT Inspector to help academic researchers. In particular, it is difficult to produce generalizable results in the study of IoT security and privacy. Although a researcher can purchase a few devices and conduct penetration tests on them in lab settings, the conclusion may not apply to diverse devices that are actually being used in consumer homes or enterprise networks.
One way to mitigate this problem is to look at network traffic from network service providers or from antivirus companies. Unfortunately, such datasets are likely to be proprietary and access may be limited to select researchers. Furthermore, the identities of IoT devices are unlikely to be labelled in such datasets; without this ground truth, it could be difficult to analyze IoT-specific traffic or make conclusions on individual types of IoT devices.
With IoT Inspector, we are the first in the research community to produce an open-source, anonymized dataset of actual IoT network traffic, where the identity of each device is labelled. We hope to invite any academic researchers to collaborate with us — e.g., to analyze the data or to improve the data collection — and advance our knowledge on IoT security, privacy, and other related fields (e.g., network performance).
Getting started
To learn more about your IoT devices and to contribute to IoT research, click here to download IoT Inspector and you can start inspecting your home IoT devices.